The recent arrest of a Samsung Electronics executive for theft of trade secrets1 was another grim reminder of a problem lurking quietly inside most modern organizations: misconduct by employees. Those who don’t focus on this topic, often referred to as “insider threat” in the United States, may be surprised to know it hides in the two top business risks that global organizations face today.
In its 2023 risk report, Allianz finds that globally, the two greatest business risks are cyber incidents and business disruption. Within those two categories, data breach is the most feared cyber incident, while a cyber-related disruption is the most feared type of business interruption2.
While we often think of external cyber attacks as the main drivers of data breaches and intellectual property theft, look no further than Tesla for an example of an insider-driven breach. In August 2023, Tesla accused two employees of providing 100GB of data, containing the identity data of more than 75,000 people, to a foreign news organization.3
Insiders are a source of cyber-related business disruptions as well. A relatively common scenario is the disaffected administrator who vindictively deletes data or changes passwords to render IT assets useless. This type of malicious attack can trigger millions of dollars in near-term outlays just to restore operations.
If insider misconduct represents a potentially strategic risk, what are organizations doing about it? Ponemon Institute’s 2022 Cost of Insider Threats Global Report found the five most common technologies used to confront insider threats are Data Loss Prevention (DLP), Privileged Access Management, User and Entity Behavior Analytics (UEBA), Security Incident and Event Monitoring (SIEM), and Endpoint Detection and Response (EDR)4.
However, it seems clear that no one has the insider threat problem solved. The Ponemon report also found the number of annual incidents has continued to increase, the average annual cost of incidents has increased from around $8M to more than $15M, and the average time it takes to contain an incident has increased from 77 to 85 days.5 Looking ahead, apparently security teams believe the most important advanced technology for threat reduction is user-behavior based tools, followed by automation and AI/ML6.
Average annual cost to an organization of
insider threat incidents in 2022 - $15MAverage time to contain an incident - 85 days
How Nuix Can Help
With Nuix Adaptive Securitysm, Nuix has taken a compelling approach to insider threat detection and monitoring that’s now getting results with customers around the world. Our strategy is to combine a unique detection capability with comprehensive, near-real time visibility into user activities. This is yielding three critical benefits for our customers. With Nuix Adaptive Security, organizations’ security teams can7 :
- Detect indicators of internal and external threats they haven’t been able to in the past;
- Receive the essential context that allows them to quickly distinguish “smoke” from “fire”; and,
Have the efficiency to operate enterprise-wide, handling many more incidents with fewer people.
Unique Detection
At the heart of the Nuix detection strategy is comprehensive logging of everything that transpires on end-user devices. This logging encompasses 12 categories of activity, from print jobs to file deletions to browsed URLs to clipboard pastes to keystrokes to name just a few. Indicators of data loss are captured, as well as many other indicators of potential misconduct. If suspicious events are detected, an automated response occurs, such as firing an alert, initiating a series of desktop screenshots, or collecting additional information and sending it to an analyst.
This level of control over what gets detected is invaluable to security teams trying to manage varying levels of risk across indicators and user groups. For example, the operator can choose to screenshot the use of high-risk keywords and simply generate an alert for medium-risk keywords. Or choose to collect files only for certain user groups. An example use is to automatically collect all Microsoft Office files copied to removable media by departing employees as a safeguard against intellectual property theft and PII leakage.
At the same time, the flexibility gives insider threat teams the ability to tailor alerting to their organization’s specific IT environment, security policies, and culture. Most importantly from my perspective, it arms the defender to change detections as user behaviors change over time. This is the difference between being blind to tomorrow’s threats and leading the pack by being ahead of the curve.
Essential Context
As those working the insider threat problem today know well, an alert that a user has exhibited suspicious behavior can raise more questions than it answers. Determining whether a particular alert is in fact a problem that requires immediate action or further investigation is one of the central challenges of insider threat detection. Nuix Adaptive Security puts the data and tools at the analyst’s fingertips to make sense of alerts. This includes a comprehensive timeline of recent user activities, built-in graphical visualization, and features to quickly dig deeper, for example by examining the file system, collecting files, and screenshotting current activity.
Efficiency
Another key challenge in detecting indicators of user misconduct is the ability to run at a large scale. Nuix provides several advantages: first and foremost is a focus on efficiency at the endpoint. Nuix runs one service, in contrast to some others using as many as 12. CPU and RAM consumption have been kept low, and the operator has the option to disable CPU-intensive checks.
Another major challenge to efficiency is false positives. Nuix detection technology provides a unique ability to eliminate unwanted alerts by fine tuning detection to exclude activity that is authorized or that security chooses to de-prioritize.
Finally, analyzing alerts—to borrow a cybersecurity term, ‘triaging’ them is another area where Nuix has a unique advantage. The management console places the right data and toolset at the user’s disposal to quickly assess whether a given detection warrants a deeper dive. This includes the ability to quickly assemble a comprehensive timeline of recent user activity, to collect data from the target user, to initiate desktop screen capture, and so on. The result is teams with Nuix Adaptive Security are doing more with less – detecting more potentially bad things without increasing staffing.
The Nuix Advantage
Customer Results
Nuix Adaptive Security is making a significant impact for our customers. A global advisory firm recently used it to detect fraud and collect evidence in a case that spanned multiple years and millions of dollars, resulting in a favorable resolution within months. Similar cases had taken years to investigate and frequently were never resolved. Large banks use our product to detect indicators of fraud and data theft that other tools have been unable to find. An enterprise customer recently discovered several software products users had downloaded and installed, some of which were involved in misconduct and all of which were previously completely unknown to the security team.
Where We Are Headed
What’s most exciting about being at Nuix is the rapid evolution of technologies across our wider stack. With Nuix Neo we are introducing automation, AI, and a consolidated user experience to PII discovery, early case assessment, and investigations of all types.
Our customers are beginning to tell us how they see endpoint technology entering this ecosystem as part of intelligent, automated investigations and risk management. This will allow a risk-indicative event to autonomously trigger data collection, processing for analysis, and risk evaluation with AI. As a result, the analyst will receive a thorough risk-based analysis of data surrounding a given incident at the start of an investigation, rather than expending most of the available time in laboring to assemble data.
If this article sparked your interest, we'd love to hear from you. Contact Hoke Smith, VP, Cybersecurity at hoke.smith@nuix.com. You can learn more about NUIX Adaptive Security at:
Additional Notes
As mentioned, NUIX has been careful to minimize agent impact on the end user. While performance varies according to environment and hardware, the data below indicate relatively low levels of peak resource consumption, even on endpoints with only 4GB of RAM.
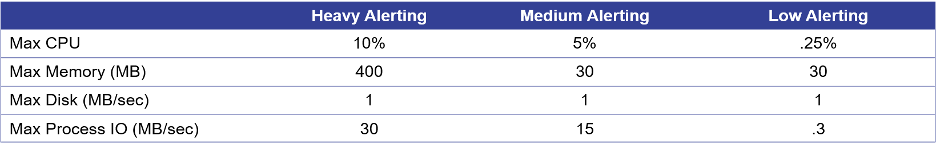
Endpoint: Microsoft ® Windows 10 Enterprise x64; 2 CPUs ; 4GB RAM
Refererences
2 Allianz Global Corporate & Specialty SE (2023). Allianz Risk Barometer: Identifying the Major Business Risks for 2023. (Link to download this report provided upon request)
3 Snider, Shane. (2023, August 21). Tesla Insider Data Breach Exposed over 75,000. InformationWeek.
4 Ponemon Institute. (2023). 2022 Cost of Insider Threats Global Report. Proofpoint, Inc., p. 20. (Link to download this report provided upon request)
5 Id.
6 Id., p. 38.


