Nuix Adaptive Security
Detect, investigate, and eliminate threats to your enterprise
Overview
Expose and control the hidden risks that threaten your sensitive data, operations, infrastructure, and workforce
Insider risk represents one of the most challenging problems for almost any enterprise today. Nuix empowers organizations to take control with a combination of precise, adaptable detection and automated next-generation investigations.
Adaptive Security empowers organizations to take control of digital risk with confidence. Built for security teams who demand visibility, speed, and precision, Adaptive Security employs a patented programable logic engine to monitor both machine and human behaviors in real time, enabling swift detection of insider risk, cyber threats, and critical compliance issues.
Adaptive Security strengthens investigations by capturing essential evidence - including screenshots, files, and multi-category event data - while seamlessly integrating with existing workflows. This flexible solution can be customized to meet specific organizational requirements, enabling security teams to make confident decisions during critical incidents.
Designed for scale with cloud-native architecture that supports the most demanding enterprise environments.
With Adaptive Security, organizations gain proactive defense against insider threats, data loss, and operational disruption—before they cause harm.
Benefits
Benefits
Automates detection, investigation, and response to focus analysts on the most critical incidents and questions
Expose risks before they threaten your enterprise
Proactively identify unauthorized activities and high-risk behaviors through advanced threat detection, and support investigations with real-time forensic monitoring and analysis.
Automate detection, response, and investigation
Harness automated intelligence to streamline security operations - from collecting event telemetry and visual evidence to scanning data flows for high-risk content. This automated collection and analysis ensures critical evidence is captured and preserved when it matters most, and supports a seamless integration with Nuix Neo for next-generation investigations.
Configure precision threat detection tailored to your organization's specific security requirements and risk profile.
The Nuix patented Engine Filter Language delivers precise, targeted detection of critical security threats, focusing resources on the most significant behavioral risks. Tailor detections to your specific requirements—fully in-house, with no dependence on external parties, and no disclosure of internal strategies.
Streamline security operations with an intuitive interface
Accelerate threat detection and incident response through a modern, web-based platform that accelerates triage, simplifies workflows, minimizes training requirements, and enables rapid decision-making.
Scale your digital evidence collection
Deploy flexible, enterprise-wide data collection for investigations, compliance requirements, and eDiscovery demands. Advanced targeting capabilities allow precise gathering of files and folders based on multiple criteria - including MAC times, filenames, paths, and hash values. Seamlessly transfer evidence to both cloud and on-premise locations in native or forensic formats, and initiate investigations at the push of a button.
Features
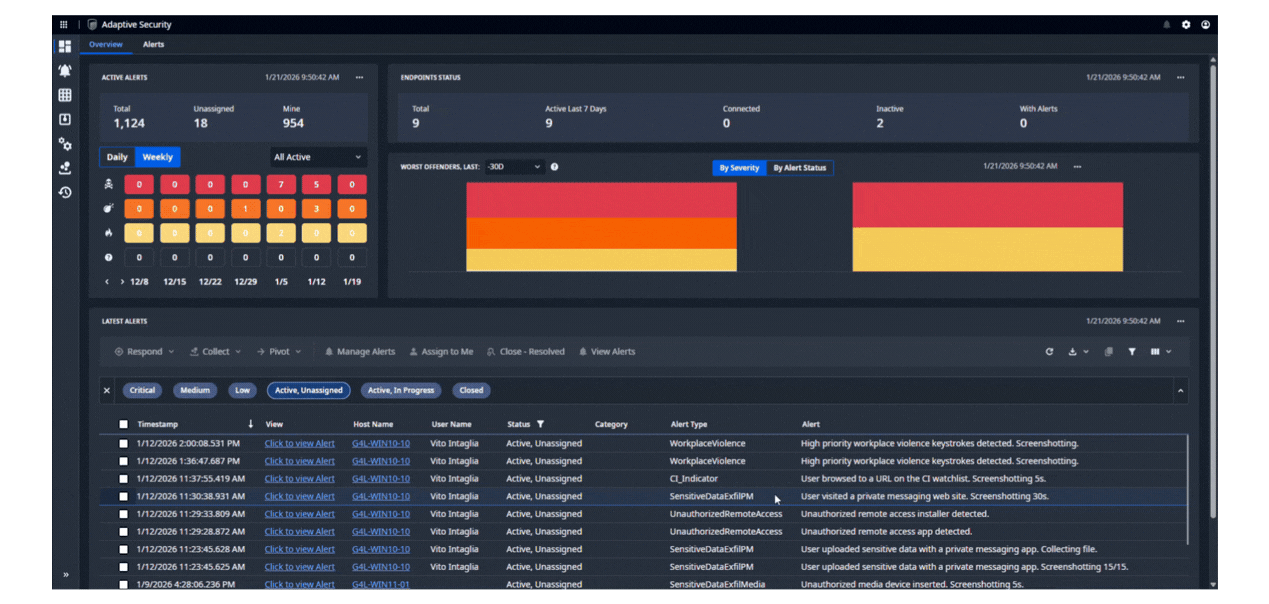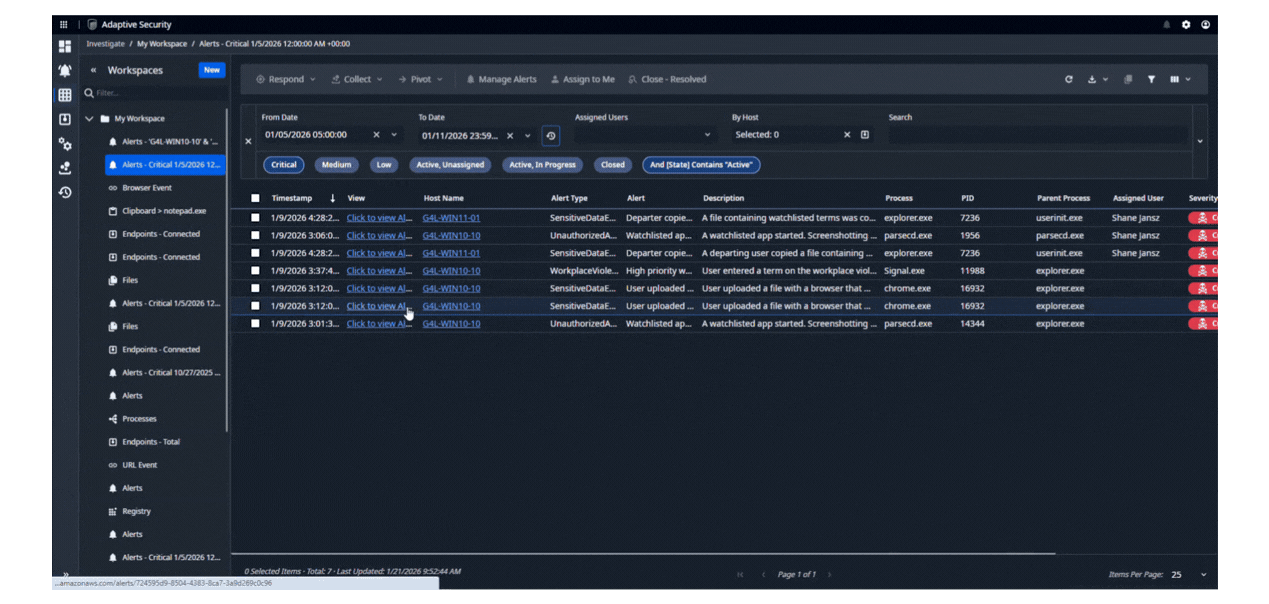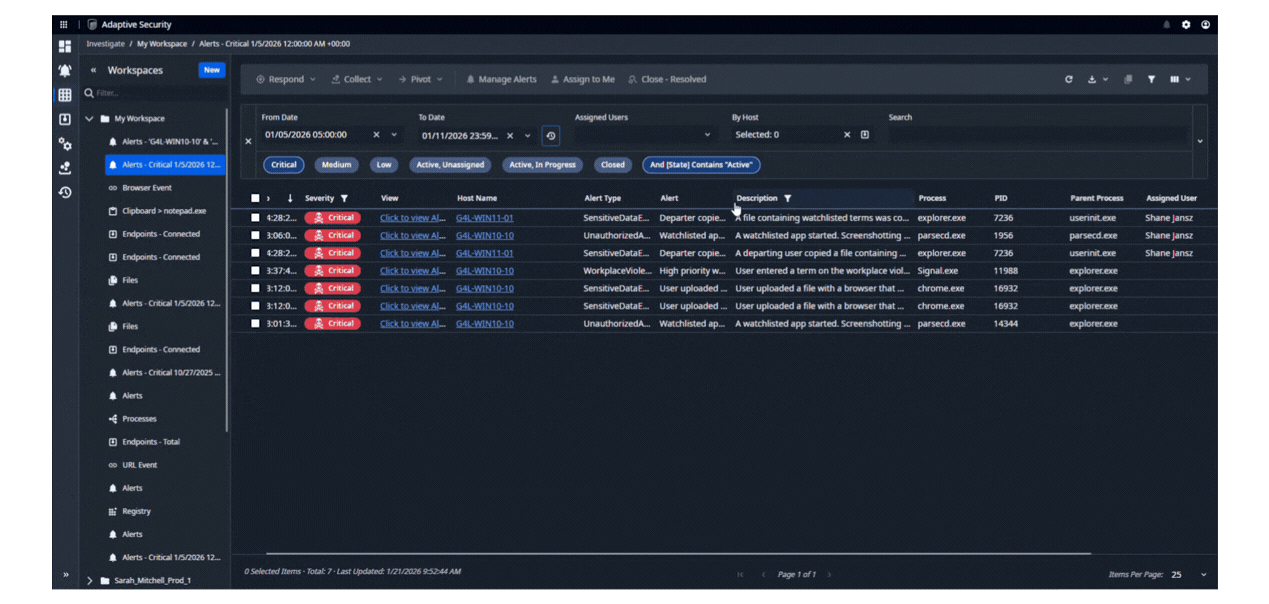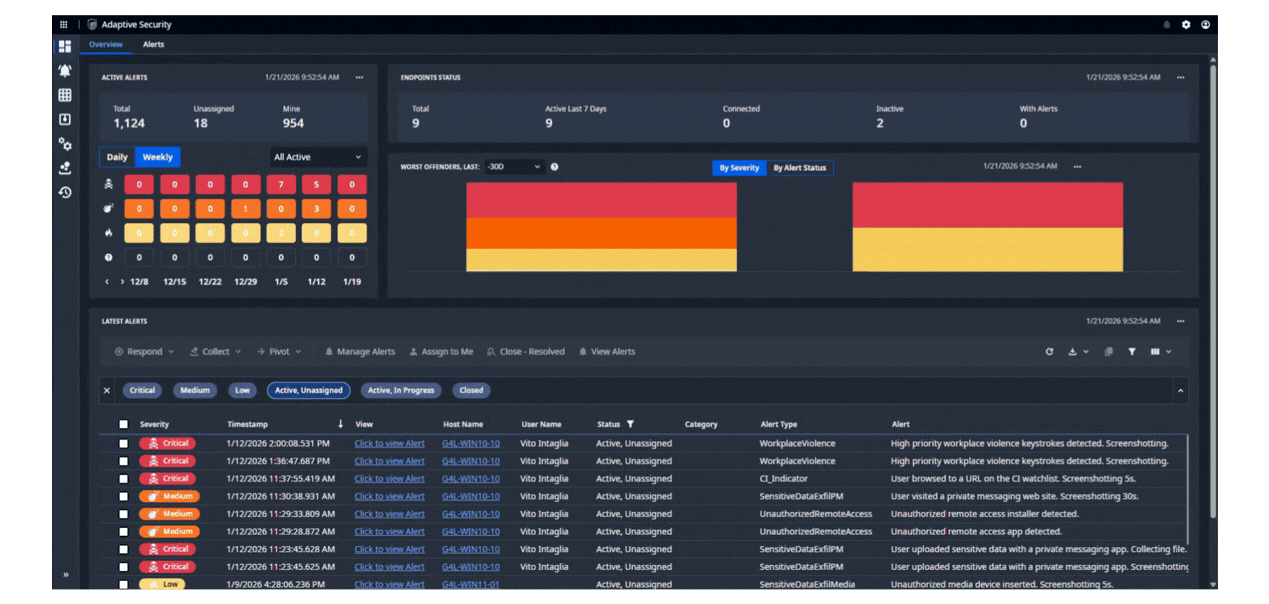
DETECT RISK IN REAL TIME
Nuix Adaptive Security detects and alerts on high risk user behavior when it happens, protecting your enterprise from the strategic risk of intentional and unintentional insider threats. Using a patented Logic Engine, Adaptive detects the subtle indicators other solutions miss and offers industry-leading customizability and control, to focus on the priority issues.
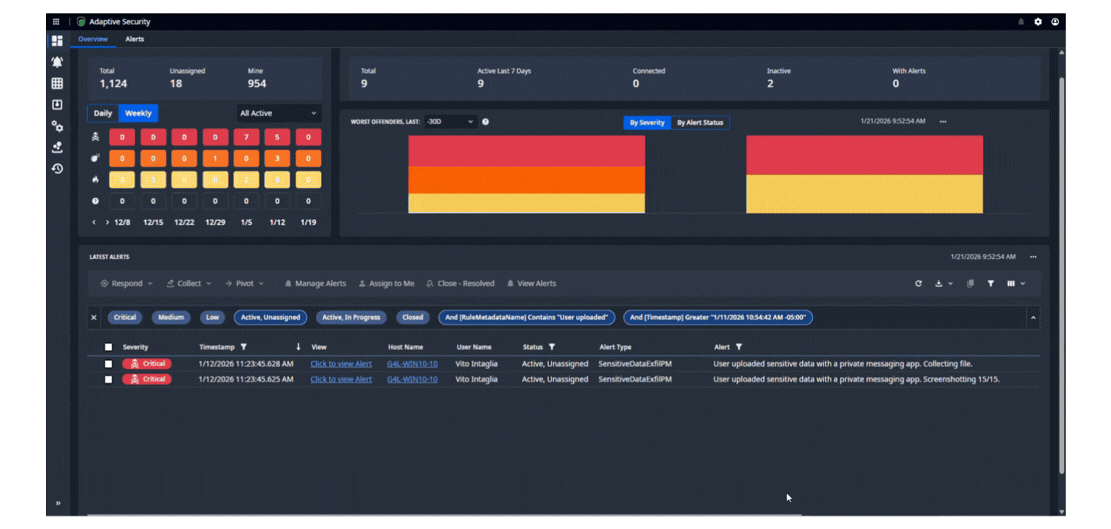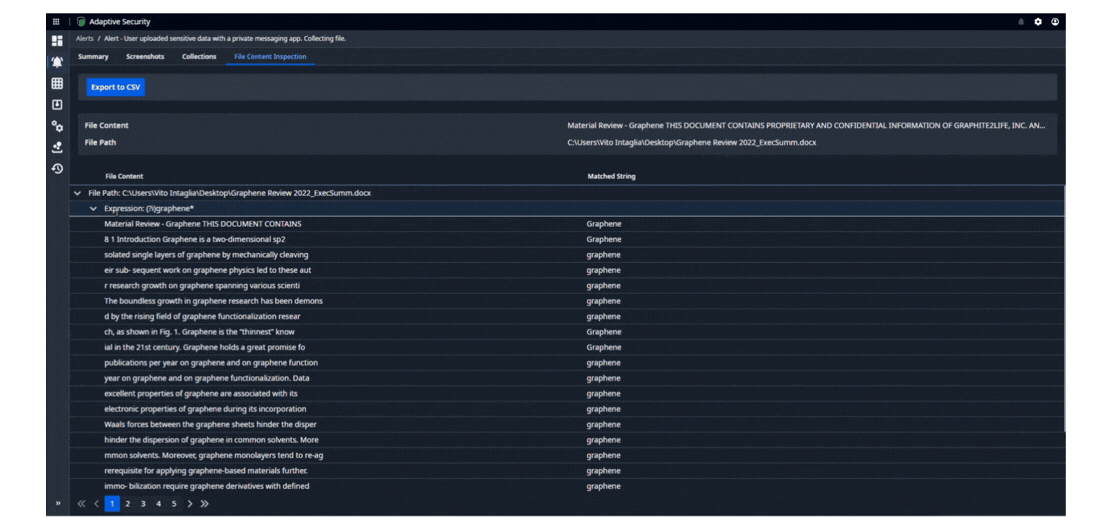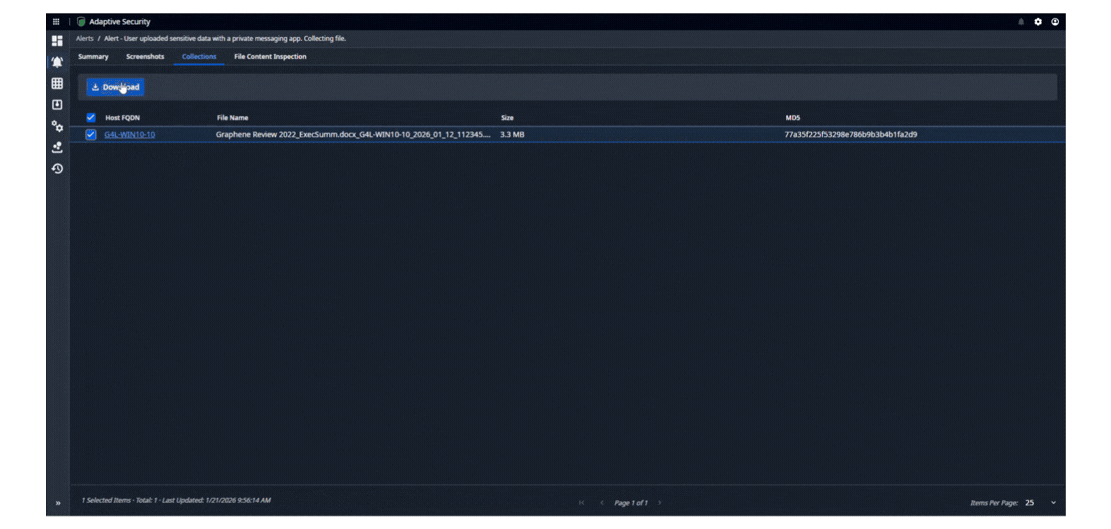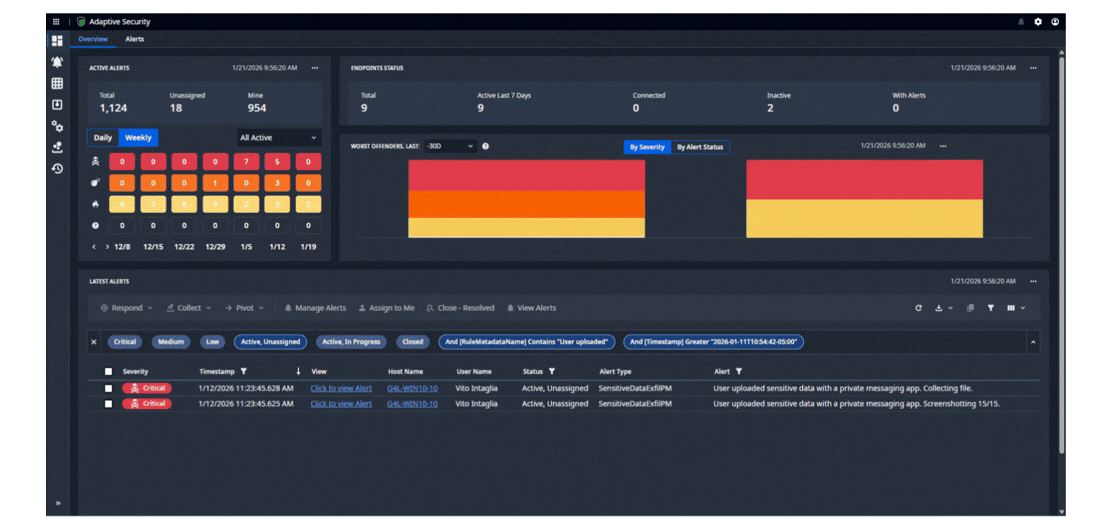
AUTOMATE RESPONSE TO CRITICAL events
Automatically take action when threatening events occur. Screenshot user behavior, inspect documents in motion for sensitive data and retrieve them, block applications and removable media, suspend internet access, and take other automated actions in response to user behavior. Tailor responses to your policies and user populations. Incorporate protection and prevention into User Activity Monitoring to control insider risk.
Use Cases
Use Cases
Enterprise-wide insider risk detection
Detect and alert on high risk user behavior including sensitive data theft, misconduct, indicators of workplace violence, employment fraud, counterintelligence / counterterrorism indicators, and harassment. Actively monitor departing users, privileged users, and teams with access to sensitive data.
Compliance monitoring
Monitor your systems for unauthorized data including information subject to litigation, personally identifiable information, personal health information, and other sensitive files. Remediate stray documents.
Data collection
Retrieve data from endpoints across your enterprise. Target data based on a full range of selection criteria. Collect files and folders to a range of destinations and container types.
Speak to an expert or request a demo TODAY
See for yourself how our innovative software can transform your data into actionable intelligence and help answer your biggest data challenges.
If your browser is experiencing any issues with the form on this page, click here to open it in a new window.

